Talking to companies about security is what we do, and we’ve been doing it for nearly 25 years. Over the years we have had some interesting engagements with some very prominent companies. Many of the companies we have serviced have had very comprehensive security programs in place and have utilized the latest in…
Throughout the years, we have conducted hundreds of penetration tests on companies across the globe. The tests we have performed have included large enterprises to small and medium sized businesses (SMB) and have taken place in practically every industry you can think of. The reasons these companies requested a…
For decades we have been providing penetration testing services for companies across the globe. From small businesses to large enterprise organization and those between, we’ve served them all. Many of the companies we serve receive penetration tests annually, in some cases even twice a year, while others are receiving…
This is part 2 of my last post “size doesn’t matter to a hacker”. Previously I pointed out why both large enterprise and SMBs are at risk of cyber-attack for different reasons, in today’s blog I will shed some light on what I believe both sizes can do to help reduce the probability of attack. Let’s start with…
Scenario #1 So, you work in a large or enterprise sized company in the IT team. You have an enormous budget and feel that you’ve got everything in place to keep you out of the hacker’s line of fire. You have all the big brand security solutions in place. You have a dedicated IT team that’s focused on security, and an…
So, you’ve finally got budget approval for your security, the downside is it is less than you wanted. Where do you spend it? What can you do to minimize your company’s exposure to attack while at the same time conserving as much budget as possible? I’d like to offer practical and actionable advice. For over 27 years…
Penetration testing, or ethical hacking as it is sometime referred to, has been around since the 1960’s. In 1971 The US Air Force adopted penetration testing to evaluate the security of their time-shared computer systems. Then, in the 1980’s the US Navy began ethical hacking tests to determine how easily terrorists…
Why are Small & Medium Business (SMBs) in the cross hairs of hackers? Many would assume that these aren’t prime targets, but statistically speaking, SMBs are at great risk, and hackers spend a significant amount of time trying to pick their locks. Here are some statistics courtesy of Purplesec 43% of cyber attacks…
Information Technology (IT) Security is BIG business. In fact, a source from Precedence Research says, “the global security market size was estimated at USD 143.07 billion in 2022 and it is projected to reach around USD 317.57 billion by 2032, poised to grow at a CAGR of 8.3% during the forecast period from 2023 to…
Over the past 27 years, we have had hundreds of conversations with companies that have experienced a cyber security incident. These incidents have ranged from unauthorized access to data theft, ransomware, phishing, corporate espionage, extortion and more. Through conversation, we’ve learned that many of these…
For as long as I have been in security, there’s been one reaction after a company gets breached, and that is they suddenly see the value in security and a budget to support it, magically appears. Sadly, this is all too common with companies that consider security an afterthought, or those that place it at the bottom of…
Why Phishing? Hackers have been phishing for information since the late 90’s, and the number of attacks has increased, for good reason: phishing attacks work! Since the dawn of time, humans have been the cause and effect of all things good and bad. They are, in terms of security, the weakest link in the security chain…
Complacency is a feeling of quiet pleasure or security, often while unaware of some potential danger, defect, or the like; self-satisfaction or smug satisfaction with an existing situation, condition. Complacency to a bad actor is like prey for a predator. It is what most hackers count on when singling out a victim…
As most know, the SecuSolutions team are strong advocates of penetration testing and red teaming. It’s a sizable chunk of our business and growing month over month thanks to the referrals and repeat business we are enjoying; however, it’s not always smooth sailing. The Good Depending on which side of the aisle you’re…
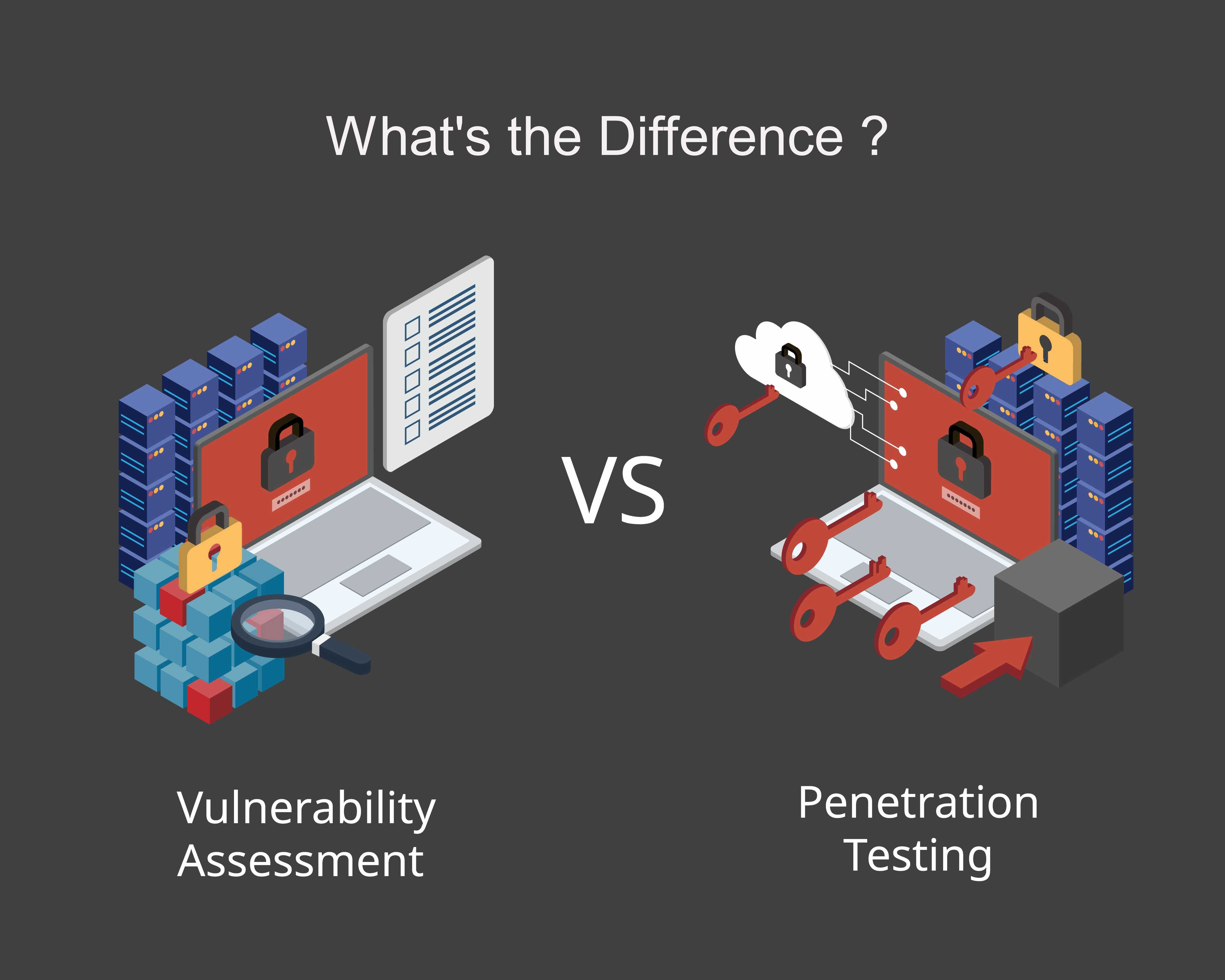
A Vulnerability Assessment is NOT a Penetration test. Don’t be misled, it could be a costly mistake. Before starting my first security company in Japan in 1999, a security administration tool called Satan was released. This appears to be the first assessment tool made available to scan networks and identify possible…
Marketing is a masterful art. It works on each and everyone of us in different ways. It could be an advertisement on a car you’ve been dreaming of, or it could be a new gadget you think you may need. It might be a motorcycle or a new RV but whatever it is that got you to buy, clever marketing has played a role in it…
Isn’t it interesting that despite all the statistics that suggest humans are the weakest security link, many organizations turn a blind eye to the importance of providing their staff with information security (InfoSec) awareness security training or the tools to help them defend the corporation they work for? Many of…
For the past 27 years (and likely the foreseeable future), executive leadership and the IT Department have seen things differently… a lot differently. This stems mainly from the fact that executive management does not completely understand the needs of the IT department, and the IT department feels the same way about…
For the last nearly 23 years of running a cybersecurity company, one thing has remained consistent and that is that IT staff, sys admins, network admins, love to hate security personnel. I say this because of the countless times we have been hired by companies to provide a security service only to be met with a line of…
There is no doubt that the pandemic has caused great hardships on people, the economy, and a host of other things that we may not feel the impact on for months and or years to come. There is no doubt that the pandemic has caused great hardships on people, the economy, and a host of other things that we may not feel the…
Did you know that in the post-COVID world, there is an accelerated and necessary adoption of digital technologies throughout the industrial world in the quest of operational advantage and excellence? The Hackett Group reports that adoption of supply chain network design and optimization tools, are expected to grow from…
October is here, that time when additional attention is brought to the importance of cybersecurity. For some companies, it’s the time to reaffirm their commitment to the plans they already have in place or the strategies they intend on launching to further the defense against cyber-attack. For other companies…
Have you ever wondered; how strong your passwords really are? Are eight characters enough, or should you use twelve? The answer is neither, is necessarily the “right” answer. This is due to password cracking. Password cracking is a method of attack where cybercriminals attempt to “crack” or steal passwords from their…
Did you know, your procrastination could cost you more than security would? The price tag for indecision, is very costly, yet many remain complacent when it comes to security. Over the past 21 years, working in the IT security sector, we have heard every excuse in the book about the reasons why security budgets get…
Nobody can deny that the business of cybersecurity has become one of the hottest and in-demand segments in the IT marketplace. It is clear that the criminal element can conduct their activities globally with ease and little chance of apprehension. In a rapidly growing and evolving digital revolution the future is…